Most organizations (Customers or Clients) prefer DevOps practices to develop products and applications since DevOps methodologies, developed as part of cyber security services, are faster and ensure better product quality and delivery. So, it is a high priority to consider the security practices to incorporate across the DevOps phases.
This helps to achieve end-to-end security of products and ensure Zero Trust requirements. By following the DevSecOps practices, we can define a standardized framework to incorporate the practices with DevOps phases.
What is DevSecOps?
DevSecOps = Development + Security + Operations.
It is considered an overarching approach offered by cyber security service providers for product and application development.
- It is a process and approach that incorporates security activities across all the DevOps phases.
- It is a process and approaches to automate the security activities and implement them in CI/CD pipeline stages.
- These automation approaches include security compliance, security monitoring, security dashboards, etc.
Note: Below mentioned graph shows the DevOps market trend increasing across all the IT industries domains. So, it is necessary to implement a standardized DevSecOps framework and practices to incorporate with the DevOps phases so that it will help follow and incorporate them in all the domains in IT industries.
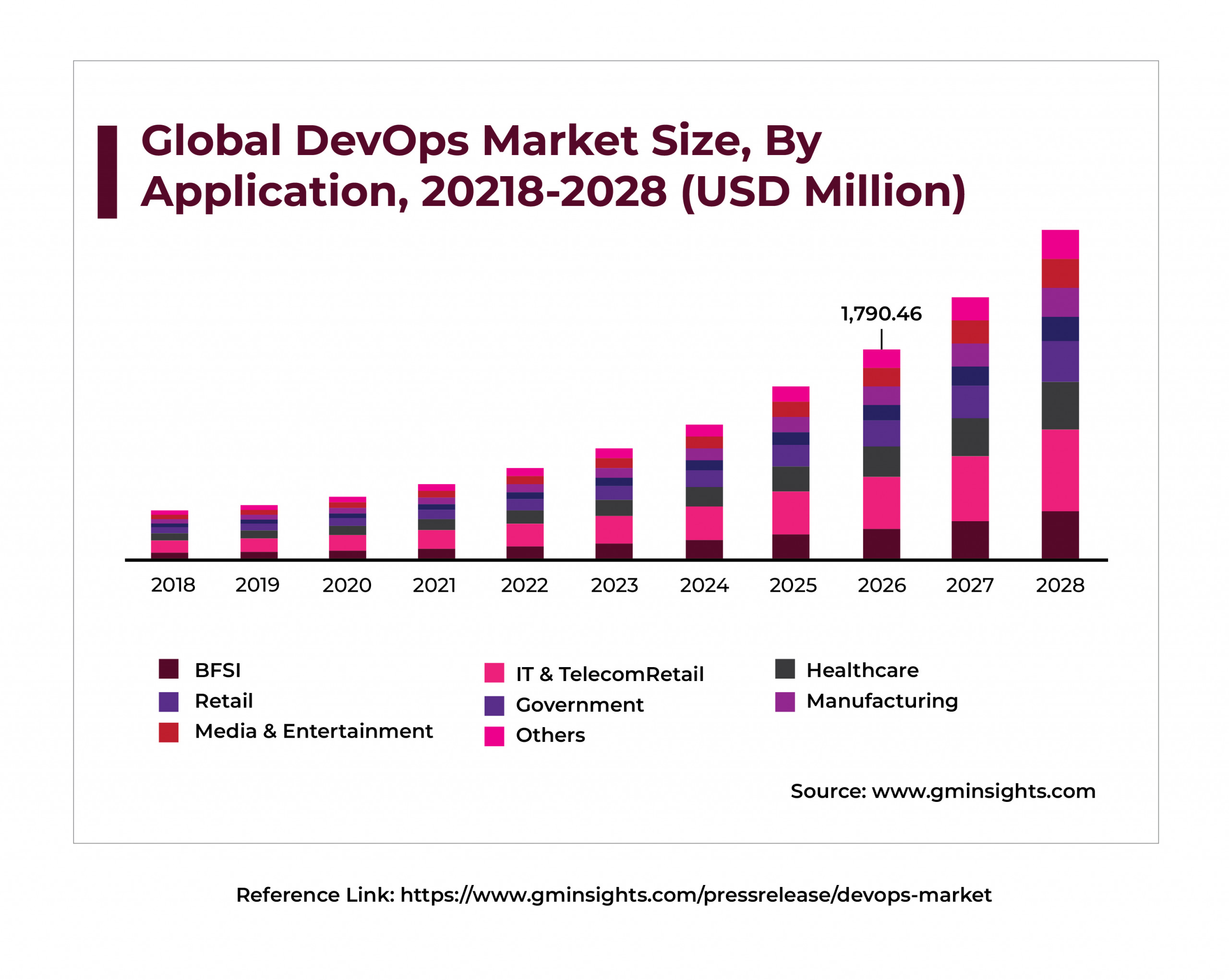
Reference Link: https://www.gminsights.com/pressrelease/devops-market
Current Problem Statements or Challenges
Here are a few of the hurdles that organizations working on product and application development face during their operations:
- Lack of a standardized DevSecOps framework and practices to follow and incorporate in the DevOps phases.
- Lack of standards and guidelines to implement the DevSecOps framework.
- Most organizations are not considering end-to-end security practices to achieve Zero Trust as part of the DevOps due to the unavailability of a proper DevSecOps framework.
- Lack of security automations and lack of CICD pipeline stages for security in DevOps.
- Security Compliance and Monitoring activities are not implemented as part of the DevOps pipeline staging.
- Security requirements and Architect practices are not implemented as part of the DevOps pipeline staging.
Solutions Proposed
As the world moves towards a more digital-first approach, with a particular focus on cyber security services, organizations aiming to offer state-of-the-art IT solutions must keep cyber security at the center of all their products, applications and processes.
Some of the ways they can achieve that are given below.
- Introducing a DevSecOps framework with standardized approaches to follow and implement the practices as part of DevOps.
- Define the guidelines in the framework to implement end-to-end security automations and integrate the security stages as part of the CICD pipeline.
- Define the guidelines in the framework to implement the DevSecOps security automations for security requirements, Security Architecture Guidelines, Threat Model, Risk Assessment, Privacy Impact Assessment, SAST, SCA, DAST, Penetration Testing, Vulnerability Scan, Security Compliance, Dashboard, Hardening Scripts and integrate these automations with the CICD pipeline.
Importance of the Solution
The global DevSecOps market size was valued at USD 2.79 billion in 2020.
It is expected to expand at a compound annual growth rate (CAGR) of 24.1% from 2021 to 2028.
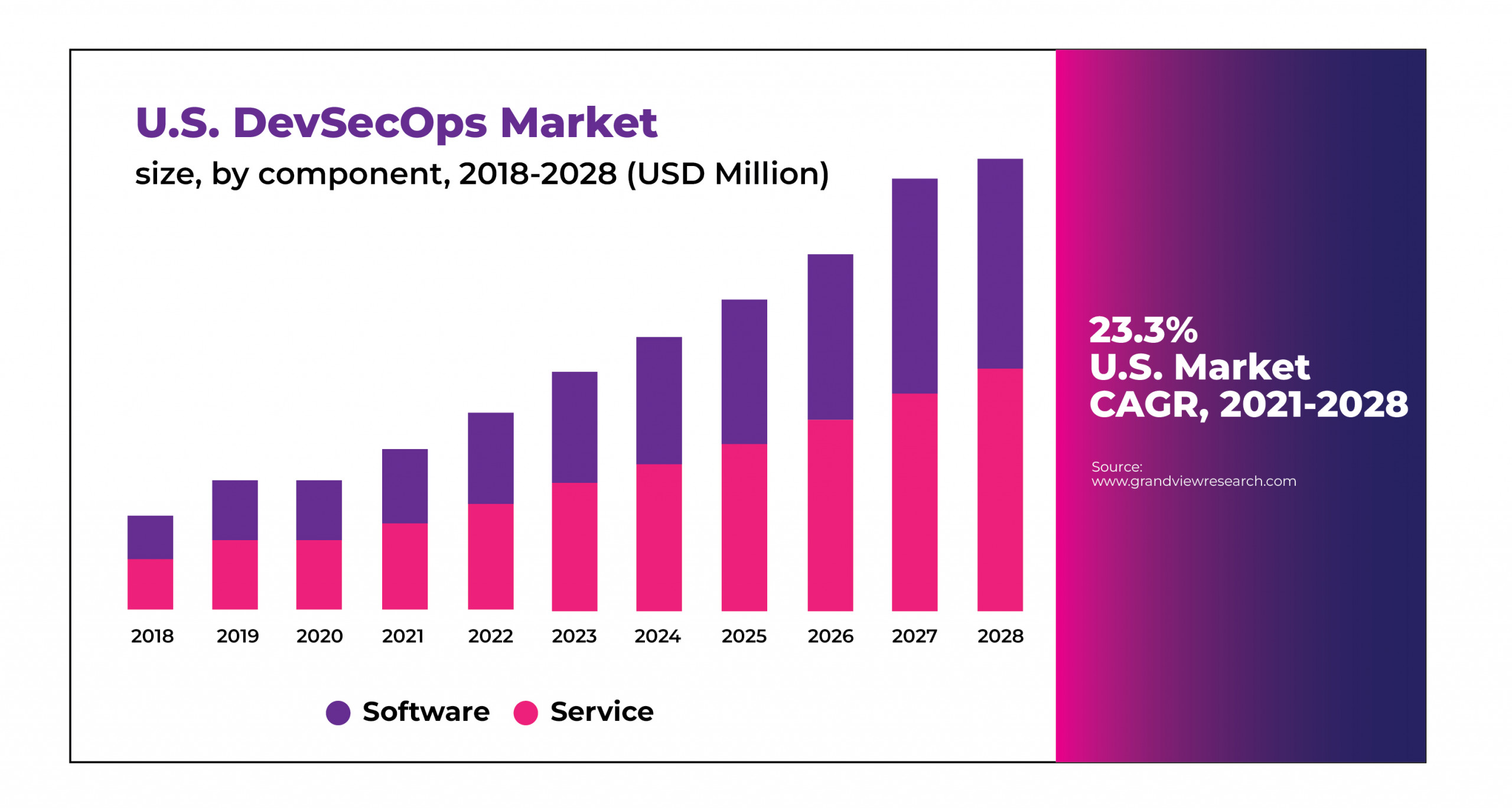
https://www.grandviewresearch.com/industry-analysis/development-security-operation-market-report
Future Perspective
In today’s fast-paced software development landscape, ensuring the security and privacy of applications is paramount. To address this challenge, the implementation of comprehensive DevSecOps automation has emerged as a vital approach. This method goes beyond conventional security practices, streamlining the development process while maintaining robust security measures.
The end-to-end DevSecOps automation can be implemented for Security requirements, Privacy requirements, Security Architecture guidelines, Threat Model, Risk Assessment, Privacy Impact Assessment, SAST, SCA, DAST, Penetration Testing, Vulnerability Scan, Security Compliance, Dashboard, Hardening scripts etc. This automation shall be integrated with any CICD pipelines.
The sample architecture diagram of the DevSecOps automation details is mentioned below:
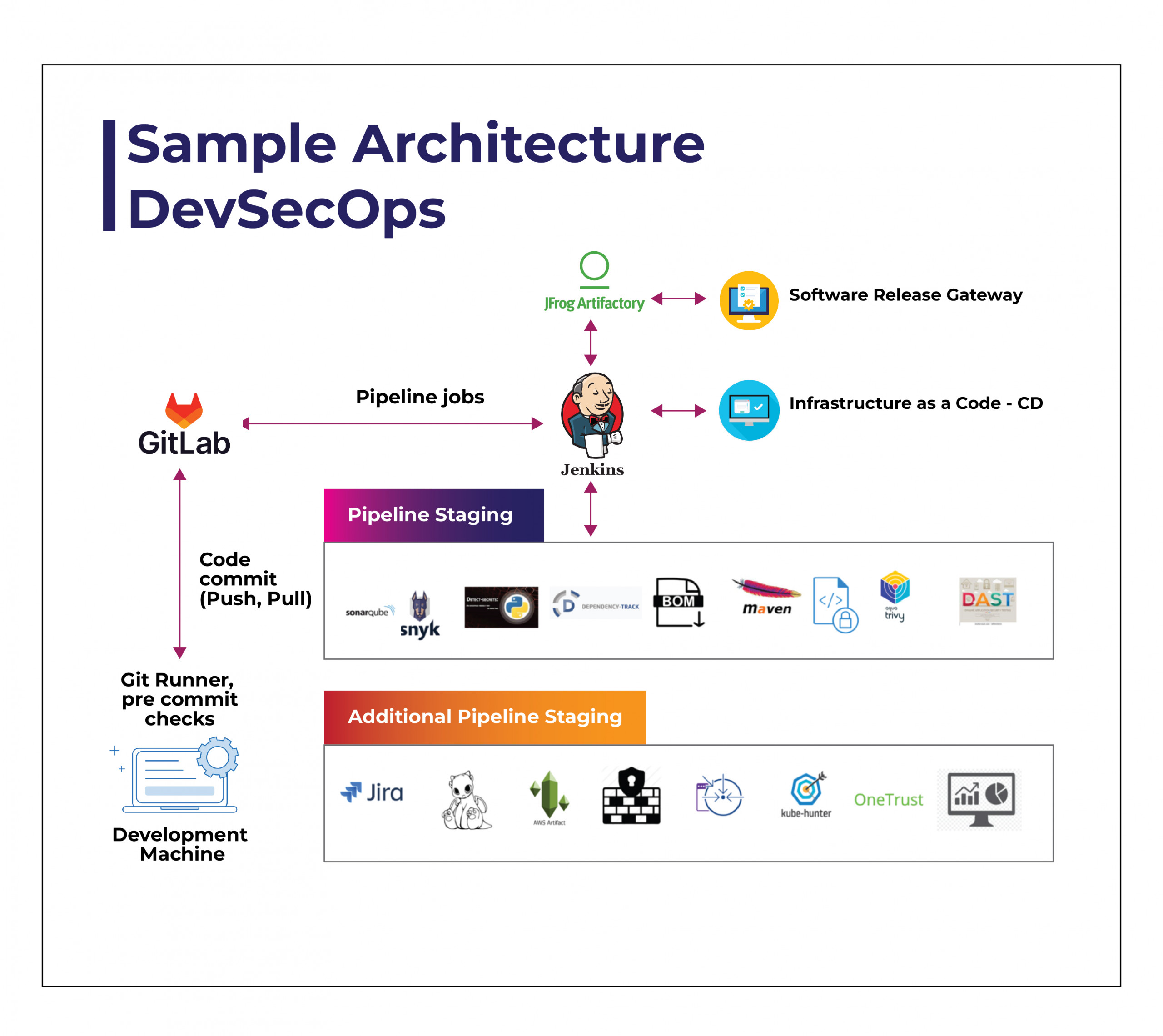
| SLNO | Security Activity | Tool to be used for Automation | To be integrated with the CICD Pipeline |
| 1 | Security Requirements | Custom automation | YES |
| 2 | Privacy Requirements | Custom automation | YES |
| 3 | Security Architecture guidelines | Custom automation | YES |
| 4 | Secure design rules | YES | |
| 5 | Threat Model | OWASP Threat Dragon | YES |
| 6 | Risk Assessment | Custom Automation | YES |
| 7 | Privacy Impact Assessment | OneTrust / Custom Automation | YES |
| 8 | Secure Design Rules | Custom Automation | YES |
| 9 | Static Application Security Test (SAST) | Snyk | YES |
| 10 | Software Composition Analysis (SCA) | Dependency Tracker | YES |
| 11 | SBOM Generation | Dependency Tracker | YES |
| 12 | Software Signing | Code signing tools | YES |
| 13 | Containerized Image Scan | Snyk | YES |
| 14 | Docker & Kubernetes Scan | Kube hunter, Kube bench, Kube audit | YES |
| 15 | Dynamic Application Security Test (DAST) | Burpsuite, KALI Linux Tools | YES |
| 16 | Penetration Testing | Burpsuite, KALI Linux Tools | YES |
| 17 | Vulnerability Scan | Qualys, Nessus | YES |
| 18 | Hardening Script | Custom automation | YES |
| 19 | Security Compliance | Custom Automation | YES |
Based on the requirements, the automation stages shall be created in the CICD pipeline.
Where Can DevSecOps Be Used?
A security-first approach in DevSecOps is the methodology that will drive efficient and secure business practices in the future. This can be followed by any of the DevOps-based product development such as for web applications, Rest API, Mobile Applications, Desktop Applications, Embedded Applications, Embedded devices, Cloud solutions, Containerized applications, etc.
Operational Benefits
While the traditional DevOps approach was good, the proliferation of cyber threats prompted the creation of the DevSecOps approach to ensure firms offering cyber security services in USA and other countries prioritize security across all levels of product and application development.
Here are the merits generated by adopting this modern approach:
- Product can achieve end-to-end security.
- Products can achieve the Zero Trust requirements.
- Products can adhere to any security and regulatory compliances.
- Low-cost security solutions and practices.
- Better quality and fast delivery.
- Organizations can improve their competency in security.
- Improves customers’ trust in security.
- Improves security competency for organizations.





