Overview
Organizations are following SDLC or PDLC to develop the product and it is necessary to incorporate the security end-to-end activities for the development life cycle. So, it is necessary to define a standardize a secure SDLC framework to incorporate the security activities across the SDLC phases.
The security activities shall be followed different types of activities like Security Requirements, Privacy Requirements, Secure Architecture guidelines, Secure Design Rules, Secure Coding Guidelines, SAST, SCA, SBOM, DAST, Penetration Test, Fuzz Test, Hardening guidelines and configuration, Vulnerability Scanning, Patch upgradation etc.
What is Secure SDLC?
It is a process and a set of practices to incorporate security activities across the SDLC phases. It also automates security activities and implements them. These automation approaches include security compliance, security monitoring, security dashboards, etc.
Current Problem Statements or Challenges
A secure SDLC framework is crucial to address evolving cybersecurity threats and ensure robust software development. By integrating security throughout the development lifecycle, it proactively identifies and mitigates vulnerabilities, reducing breach risks, adhering to regulations, building trust, and saving resources. In a landscape of frequent cyberattacks, this approach safeguards data, user privacy, and system integrity effectively.
Here is a list of the current challenges that a secure SDLC framework aims to alleviate:
- Lack of standardized Secure SDLC practices to follow and incorporate in the in the development phases.
- Lack of standards and guidelines to implement the Secure SDLC framework.
- Most of the organizations are not considering end-to-end security practices to achieve Zero Trust as part of the Secure SDLC
- Lack of security automations to execute the security activities across the SDLC.
- Security Compliance and Monitoring activities are not implemented as part of the development of life cycles.
Solutions Proposed
To ensure software developed by organizations align with the client’s requirements of security, reliability and regulatory compliance, here are a few options to explore that can prove effective:
- Introducing a Secure SDLC framework and defining the end-to-end security activities to incorporate as part of the SDLC.
- Define proper guidelines to execute the security activities such as security requirements, Security Architecture Guidelines, Threat Model, Risk Assessment, Privacy Impact Assessment, SAST, SCA, DAST, Penetration Testing, Vulnerability Scan, Security Compliance, Dashboard, Hardening Scripts etc.
- Automate the security activities and reuse these automations for any of the application or product developments. Automations for security requirements, Security Architecture Guidelines, Threat Model, Risk Assessment, Privacy Impact Assessment, SAST, SCA, DAST, Penetration Testing, Vulnerability Scan, Security Compliance, Dashboard, and Hardening Scripts are some of the primary ones.
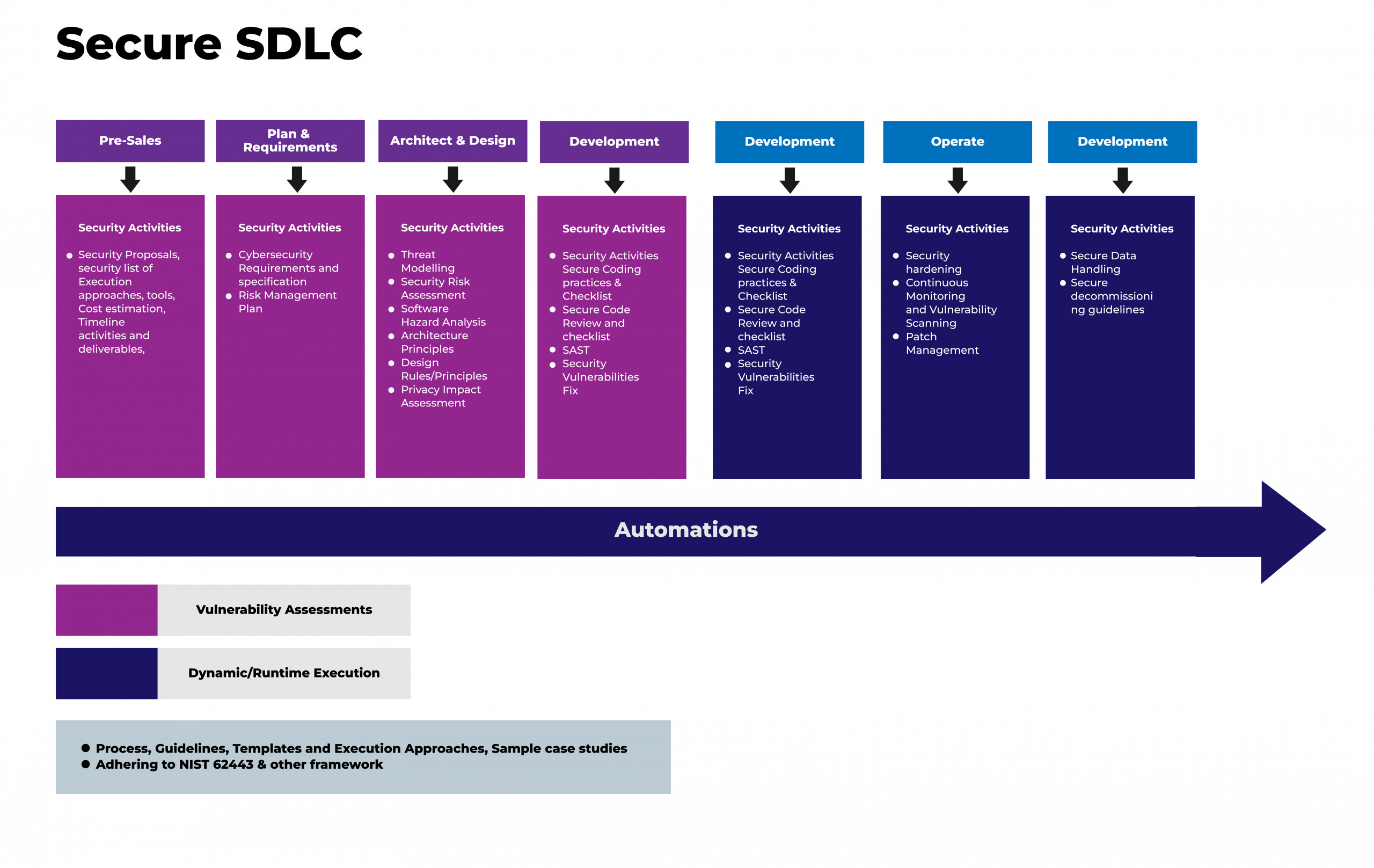
Secure SDLC Overview
Future Perspective
A comprehensive SDLC framework based on security with end-to-end automations can be implemented for Security requirements, Privacy requirements, Security Architecture guidelines, Threat Model, Risk Assessment, Privacy Impact Assessment, SAST, SCA, DAST, Penetration Testing, Vulnerability Scan, Security Compliance, Dashboard, Hardening scripts etc. This automation shall be incorporated as part of the SDLC.
| SLNO | Security Activity | Tool to be used for Automation | To be integrated with the SDLC |
| 1 | Security Requirements | Custom automation | YES |
| 2 | Privacy Requirements | Custom automation | YES |
| 3 | Security Architecture guidelines | Custom automation | YES |
| 4 | Secure design rules | YES | |
| 5 | Threat Model | OWASP Threat Dragon | YES |
| 6 | Risk Assessment | Custom Automation | YES |
| 7 | Privacy Impact Assessment | OneTrust / Custom Automation | YES |
| 8 | Secure Design Rules | Custom Automation | YES |
| 9 | Static Application Security Test (SAST) | Snyk | YES |
| 10 | Software Composition Analysis (SCA) | Dependency Tracker | YES |
| 11 | SBOM Generation | Dependency Tracker | YES |
| 12 | Software Signing | Code signing tools | YES |
| 13 | Containerized Image Scan | Snyk | YES |
| 14 | Docker & Kubernetes Scan | Kube hunter, Kube bench, Kube audit | YES |
| 15 | Dynamic Application Security Test (DAST) | Burpsuite, KALI Linux Tools | YES |
| 16 | Penetration Testing | Burpsuite, KALI Linux Tools | YES |
| 17 | Vulnerability Scan | Qualys, Nessus | YES |
| 18 | Hardening Script | Custom automation | YES |
| 19 | Security Compliance | Custom Automation | YES |
Where Can the Framework Be Used?
After a secure SDLC framework is developed after thorough research and consideration of all the factors, it can be followed by any of the product development processes such as for web application, Rest API, Mobile Application, Desktop Application, Embedded Application, Embedded device, Cloud solutions, Containerized applications, etc.
Benefits of a Secure SDLC Framework
When enterprises adopt an SDLC framework, they can avail the following advantages:
- Products can achieve end to end security.
- Products can achieve the Zero Trust requirements.
- Products can adhere to any security and regulatory compliances.
- Low-cost security solutions and practices.
- Better quality and fast delivery.
- Organizations can improve competency on security.
- Improves customers’ trust in security.
- Improves security competency for organizations.
On a Final Note
The imperative for building next-gen software within a Secure SDLC framework is underscored by the ever-evolving landscape of cybersecurity threats. With traditional development methodologies proving inadequate in addressing modern security challenges, the integration of security measures throughout the development lifecycle becomes paramount.
By aligning security practices with software development, a Secure SDLC framework addresses vulnerabilities proactively, mitigates breach risks, ensures regulatory compliance, fosters trust, and optimizes resource allocation.
Ultimately, the integration of security into software development through a Secure SDLC framework is not just an option; it’s a strategic imperative in safeguarding digital assets and maintaining a robust cyber defense posture in an increasingly perilous digital landscape.





